In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.
In the last Hacker Fundamentals, we talked about the OSI model as well as a little on TCP/IP and the protocols that make up the suite. Now, we're going to expand on that now and take a look at the various parts of a network that you might have heard about, but might not understand.

We already covered how your data travels the OSI model, layer by layer, and talks with other machines on your local network. But how does that data leave your network? How does it know where to go? What's going on here?
Much of the 'talking' on a local network are broadcasts. This computer is asking for the MAC address of another one, or asking for a local IP address, or any number of things. But doesn't that mean the Internet should be flooded with various broadcast noise all over the place? As it turns out, no. You see, the job of a router is not only to route traffic, but to stop broadcasts. To explain this concept fully, let's look into some examples.
No routers were hurt in the writing of this article.
A Tale of Two Packets: Internal
If you remember correctly, an IP address has two components, the network section and the host section. A subnet mask separates the IP address into those two segments (<network><host>). A subnet is expressed just like an IP address in a four octet form, the most common one being 255.255.255.0 where the '255' means those octets are describing the network and the '0' is describing the host.
Let's say you wanted to send data to another computer on your local network at home. Your internal IP address in this example is 172.10.1.20 and your destination IP address is 172.10.1.30. Also, let's assume your subnet mask is a standard 255.255.255.0.
The first thing that gets done is the computer looks at the address on the packet being sent. It then compares its address with the destination address. Notice the 172.10.1.x is the same on both, and the subnet mask has filled octets in the same locations as well ( 255.255.255.0). This tells the computer that the destination is on the same network it is on. Your computer knows it is host '20' and it needs to reach host '30' and it doesn't need to go through a router to get there.
Now your computer only needs to know the MAC address of host '30' to send this data on its way. If you recall the Media Access Control address is a physical layer function that addresses actual physical hardware on your computer. In a nutshell, it works like an IP address, only on your local network.
ARP!
To perform this feat, your computer sends out a broadcast message to everyone on the network called an ARP, or Address Resolution Protocol. It's like your PC yelling "HELLO! I am looking for the computer 172.10.1.30".
Now each device on the network receives that message and looks at its own IP address in turn. The router (172.10.1.1) sees it is not the one being looked for and drops the message. Other computers on the network do the same thing until the computer that has the IP of 172.10.1.30 gets it, checks its address, and sees they match. It then replies back to the sending computer of 172.10.1.20 saying "HEY! That's me and my MAC address is AA00:BC33:3211".
In the picture below, the MAC address is called an "Ethernet address", reflecting the fact that it's addressing for the physical layer. However, common lingo is "MAC address".
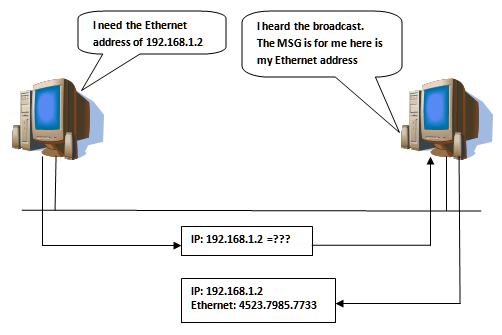
Now the sending computer has the internal IP and MAC address of the receiving computer and can send its data over. But what happens if the two addresses are not on the same network?
A Tale of Two Packets: External
Well, it's not as simple when we have to cross other networks, as there is a bit more going on behind the scenes, as you will see. Let's assume we are sending the same data as before and our source IP address is 172.10.1.20 and our destination IP address is 192.168.0.100. You should immediately notice by the subnet mask of 255.255.255.0 that these two addresses are on separate networks. See, we are getting there.
Just like in the first example, the sending computer looks at the destination address and compares it to its own. However, this time there is a problem—they don't match at all.
Now it knows that it can't just send out an ARP message like before, because remember what happened in the last example, when the routers address didn't match the address being asked? It simply dropped the packet. This is how routers stop broadcasts from traveling the entire Internet. In fact, without this design, the Internet would be flooded with so many broadcast messages from the millions of connected devices that it would crash and fail.

At this point, your computer knows an ARP just isn't going to cut it for the destination of 192.168.0.100, so it broadcasts another ARP. But this time is looks for what's called the default gateway. This is a node, or a router, that acts as an entry or exit point to another network.
Normally, when a computer cannot find a route for an IP address, it will send it along to the default gateway as a route of last resort. This is your modem/router at home. Your router will reply saying, "YO! I am the default gateway and my MAC address is xxxx:xxxx:xxxx!"
Your computer then adds the routers MAC address as the destination MAC address to the packet, and sends it over to the router for safe travels.
Route Me Baby!
The router takes a look at the packet and knows the source IP came from its own network. But the destination is separate altogether. Because the destination is not the same as the router's own internal IP address, it knows the packet is not for it, but needs to travel through it.

The router then looks at its routing tables to find a way to get to the 192.168.0.x network. It leaves the source and destination IP address information inside the packet, and changes the new source MAC address to its own address and the destination MAC address to the next node deducted from the routing table.
This process continues over and over with each router that picks up the packets looking at the addresses, seeing it's not for their network and passing it along until it reaches the final destination of 192.168.0.100.
That router will strip of the source and destination MAC addresses that allowed the packets to travel, and replace the source with its own. It then ARPs to find the MAC address of the server being looked for and uses the reply to add the final MAC address of that machine, then sends it along.
In Closing
Isn't that amazing? When you check your email or browse the web, this is happening all of the time, hundreds and thousands of packets traveling 10-20+ routers to span the world... all in just a few seconds.
When you are packet sniffing, you can grab this information midstream. Simply turn on Wireshark and watch and see how many packets zip around in a small amount of time.
Questions about all this? Comments? If you've got some knowledge, you can pass it onto the community—we are always welcome to it! Start a thread in our forum!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























27 Comments
this was amazing for me!
I am still learning and ingesting it all, but thanks for this :)
Glad you liked it.
OTW
I too liked it. It was fantastic
Wow, extremely helpful! I was always kind of confused when it came to subnet masks and MAC adresses.. not anymore!
I think I missunderstood something.. I just understood that if your computer sends out a package as TCP it actually does the same like in your own Network, it just sends the package at a random IP (ARP stuff) hoping that the package reaches the destination IP somewhen? It actually doesn't know where this destination IP is?
Anthony:
Welcome to Null Byte!
Let me see if I can understand your question and answer it.
When a packet is sent from your system, it has a destination IP address attached to it in its header. If that IP address is on your internal network, its simple, it delivers it to that address. The switch and router know the internal IP address of every machine by ARP.
If the packet has an IP address outside the internal network, the packet goes to the router and from there is sent out over the Internet through multiple routers until it reaches its destination.
The process is far from random. It is quite deterministic and precise.
Hope this helps.
OTW
Hi man, Sorry for My bad english, i'm an italian boy and i love and read all of yours guides! I have a question;
In the MITM we change our MAC address or we have the same MAC of the target? I read a guide about the MITM attack and i have seen that we have to sniff arp packets.. Is it right?thanks for all your manual.. The best of ever! Really! I have looked for this kind of guides, but this site is the best for me! Very Compliments!
Dark Soul:
Yes, we have to swap MAC addresses with both the client and the server so that all their traffic goes through our computer.
OTW
Ok Thanks a Lot! :)
Thanks a lot, I like examples to understand stuff! All what you said is clear, still something bothers me: once the local computer knows that the destination is on the same network, why does it not simply send the " load" after all, the arp message reaches the target, why can't he actual message do the same?
Wow it's really amazing! Thanks, you did a really good job again. It really helped me out to understand packet sniffing and how the intenet works.
great sir....
you are a TRUE GURU....
in our language
First, great guide, thanks so much !
Second, I got a question :-)
If you send a paquet over the Internet, searching the good server out of your network, does it mean all routers of the world will receive it and transfer it maybe and... Oh Gosh How Many Paquets We Got Here ?
Thanks again !
No, only the routers between you and the destination. That's usually averages about 12 and can be as little as 1 or as many as many 30.
Can we know actual number of routers, can we capture packets of other routers if we are between them and destination?
Ok now I understood everything in this guide thank you !
Great Tutorial sir :D
However is there any way to access the wireless network that has a password? and the signal came from the MODEM.
TIA I will highly appreciated if you could tell me the steps :)
More Power! :D
Even though it's a 2 year old post- Thanks a lot!
Much more to learn :)
Wow! so much info! Great article!
Hi!
This is an old post and I am a new user, so maybe you're not around anymore, however I want to thank you anyway for the time you spent putting together this post and I also would like to ask a few questions.Hopefully someone will take the time to answer if so thank you.
First, towards the end of the article you say "It leaves the source and destination IP address information inside the packet,..."but isn't this the step where our router changes-thanks to it's buddy NAT-the source IP(which is the private one) with the router's public address?
Second, I knew about Routing Tables and how every single device(not just routers) has one. I didn't realise that routers in order to communicate with each other used MAC addresses. So basically every router's default route not only does it have the IP address of the next hop but it's paramount for it to include the MAC address also, otherwise it wouldn't be able to route packets. Correct? I have never seen a MAC address in a routing table, that's why I am a bit confused.
waaoh!!....am liking this article, it very educative just learning bit by bit....Thanks man.
Wooow!!!! This is amazing, thank you so much for this, i learned a lot today. :D
the destination ip address you mentioned is server's or another computer's?
Great tutoria!
A newbie question though. Let's say I want to talk to my grandma' and she has 3 computers on her internal network. But my computer can't possibly know her internal IP address, it only knows the router's public IP address, right? So after the data got to her router, how does it know what computer to send the data to?
I liked this so much. It is very great.
Well, so far, ok. So my first question is what's the next step and what do I need to do.
Hi all,
I read the entire article and this is really helpful for the beginner. Great work, appreciate that. I do not understand this paragraph can anyone explain this to me.
Share Your Thoughts